Robocalls have become a major concern in many countries and the USA is leading this space with around 50 billion robocalls received in 2021, according to Robocallindex History. Out of all these, around 40% of calls were fraud calls. Robocalls along with caller ID spoofing are a big threat and that has been happening across countries for many years. The call recipient often finds this caller as someone they know or someone from authority and becomes an easy victim of technology that is invented for our betterment. VoIP is invented and has been going through various innovations to benefit businesses and end users, but frauds and hackers use it to meet their malicious intent. This has made the implementation of STIR/SHAKEN in VoIP solutions by VoIP software development companies or VoIP service providers necessary.
In fact, since June 30, 2021 implementation of STIR/SHAKEN standards has been made mandatory by FCC (Federal Communications Commission) in the USA to protect the interests of customers from fraud callers.
What is STIR/SHAKEN?
In simple words, it is a mechanism that is used to authenticate the identity of the caller using technology standards. It can even reject the call before reaching the recipient if the caller fails to prove that the identity used by him or her is genuine. This is a completely automated process of authenticating the caller and evaluating the trustworthiness of the caller ID, name, and number.
STIR is an acronym for Secure Telephone Identity Revisited. SHAKEN is an acronym for Signature-based Handling of Asserted Information Using toKENs (SHAKEN). These are standards defined to deploy a mechanism by a VoIP development company to assess the legitimacy of the caller.
Transform your call verification process with our STIR/SHAKEN solutions.
It is usually used by carriers for carrying out legitimacy checks for numbers for calls transmitting through their network.
What is the difference between STIR and SHAKEN?
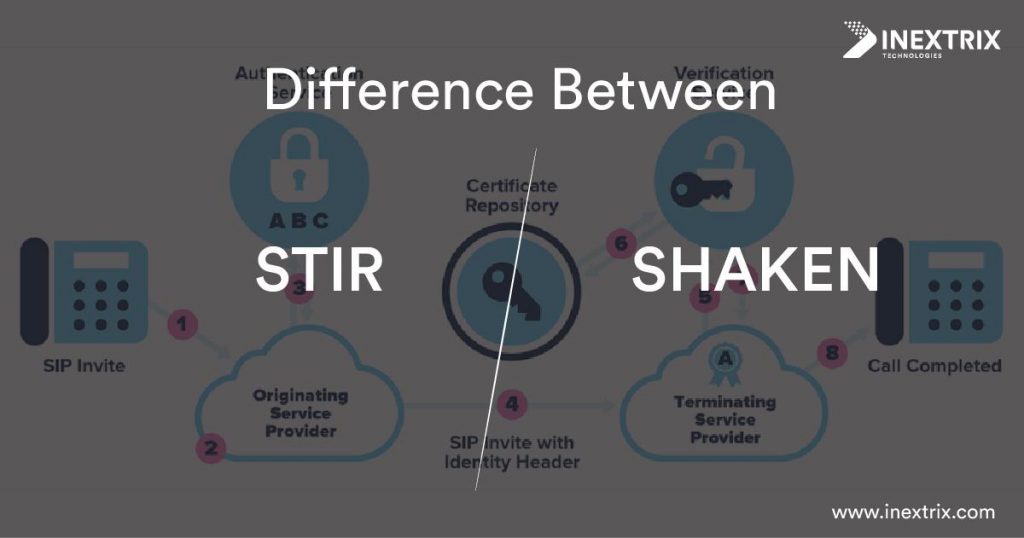
The terminology STIR/SHAKEN is often used together, which confuses many people by thinking that this is a single thing. However, there is a difference between both of them
STIR is a working group available with one of the internet standard bodies, called IETF. This group has created a set of standards, which can be used to create a digital signature for each call. This signature can work as a digital identity for each VoIP call. This digital signature will consist of details of the caller and it will also have a digital signature, which can be used for verification. This certificate can be verified at the recipient carrier and take the necessary steps to avoid robocalls.
SHAKEN is the set of standards used by VoIP software development companies or carriers to define how to deploy STIR in the network to make this process of review, verification, and authentication easy, automated, and efficient.
How does the STIR/SHAKEN Standard Work?
- Whenever a call is generated in a network, the originating carrier will receive a SIP INVITE.
- The originating carrier needs to verify the source of the call and confirm the legitimacy of the caller.
There are three possibilities to review the legitimacy of the caller, which can be implemented with Asterisk or FreeSWITCH development:
- Gateway Attestation: The carrier will only authenticate the origin of the calls such as if it has an American caller ID, whether the call originated from the USA or not. It cannot verify the source of the call.
- Partial Attestation: The carrier will authenticate the origin and also identify the call source, but there is no way to verify and authorize the source of the call. For example, if a caller is using an IP PBX solution, the carrier cannot verify the source.
- Full Attestation: This is a complete authentication of the number, source, and even calling party. This is possible if the caller is available in the subscription list or database of the carrier.
- Based on the type of identity verification, the origination carrier creates a SIP identity header for the originating call and attaches it to the certificate. This will include the following information:
- Calling number
- Called number
- Attestation level
- Call origination and
- Digital certificate
- The origination carrier will attach this digital certificate with SIP INVITE and SIP Identity header.
- At the destination, the carrier will verify the digital certificate and other details attached to SIP INVITE.
- Depending on the verification, the destination carrier will show the authentication level to the call recipient, so he or she can decide whether the caller is someone trustworthy or not and decide whether to accept or reject the call.
This makes the whole process of STIR/SHAKEN implementation easier.
How can we help you with the implementation of STIR/SHAKEN?

We are renowned for our Asterisk and FreeSWITCH development expertise. Along with developing the best VoIP solutions like an IP PBX solution, call center solution, etc., we also provide STIR/SHAKEN deployment to our clients. We are renowned as the top VoIP development company for our specialization in implementing all three different types of attestation and making this whole process seamless. We can create public and private digital certificates and even add an added layer of security to protect clients’ interests from robocalls, caller ID spoofing, and other fraud attacks on VoIP clients and users.
Concluding notes
For carriers, VoIP service providers, and even VoIP development companies, it is essential to protect customers from commonly known fraud attacks. STIR/SHAKEN is the security standard enforced by FCC and it is made mandatory for providers that want to cater to American customers. Other foreign countries are also likely to adopt STIR/SHAKEN to restrict deceptive behavior and illegal activities.
We have been helping businesses with our VoIP development services to protect their VoIP network. We, being one of the top VoIP software development companies, have helped a smart telephony platform to implement fraud detection and management software to protect customers and infrastructure from unusual activities. We also have experience in session border controller software development. STIR/SHAKEN implementation and deployment services are offered by our VoIP engineers. We also provide the required consultation to implement STIR/SHAKEN in your VoIP network. To know more about our services and how we can help you with our services, contact us.
